Table of Contents
Configuring ERSPAN packet capture for Network Security Monitoring
ERSPAN 1) stands for Encapsulated Remote Switch Port ANalayzer or just Encapsulated RSPAN. This is feature available on some of the higher end platforms like Catalyst 6500 and 7500s, Nexus, and ASR platforms. Let us see how this feature can be useful in some scenarios.
What is ERSPAN
ERSPAN allows you to capture network packets from one or more physical ports, then transmit these packets to a particular IP address where your monitoring software is waiting. The captured packet stream is sent inside a Layer-3 IP tunnel using GRE (Generic Routing Encapsulation).
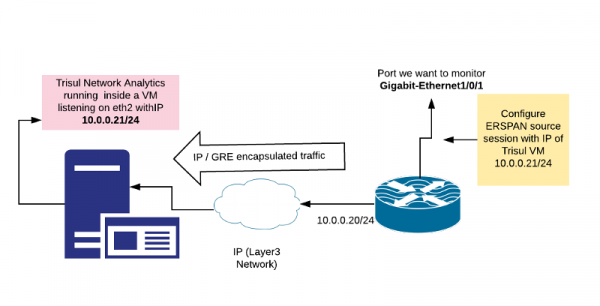
The following diagram shows a ERSPAN session that captures packets from interface GigabitEthernet1/0/1 and transmits it to the IP address 10.0.0.21 where TrisulNSM is listening.
Why ERSPAN for Network Monitoring
There are three port mirroring features in Cisco :
- Physical SPAN – this is the common port SPAN. It is supported on nearly all models of Cisco and allows you to physically mirror one or more ports to a monitor port.
- RSPAN – Remote SPAN, this is a Layer-2 port mirror where you can capture remote packets over a Layer2 VLAN and bring it across your L2 network
- ERSPAN – Layer3 Remote SPAN, this is what we are talking about in this article. Allows you to transport a port mirror session over an IP network.
ERSPAN Use case 1 : Virtual Machine
To provide network packets to Trisul Network Analytics or other NSM tool running inside a Virtual Machine. Particularly when the administrators of the VM are unable to provide a promiscuous mode physical interface.
Recently, we had a customer who was consolidating all their server systems on a Nutanix VM farm. They wanted to put TrisulNSM also on a VM on that farm instead of a physical box. Since the Nutanix does not yet support a physical port mirror at the VM level 2) , we use a ERSPAN session to get the packets directly to the TrisulVM.
ERSPAN Use case 2 : Temporary monitoring
If you are already doing ERSPAN, then adding an extra port is trivial. When you want to temporarily monitor an interface without having to do any extra cabling that would be required for a physical layer SPAN. The main disadvantage is ERSPAN is only available on high-end Cisco gear.
Configuring
In ERSPAN, there is a concept of Source and Destination session. A source session specifies interfaces from which traffic is captured and sent to an analyzers IP address. A destination session specifies the output port to which the decapsulated traffic is written out. You dont have to configure a destination session.
Here we only configure a source ERSPAN session to the IP address 10.0.0.21 of the TrisulNSM Virtual Machine. When you do this, the network will just forward the GRE Encapsulated mirror traffic to the TrisulNSM VM. Since Trisul already supports ERSPAN as a capture mechanism, you can use that to decode the traffic. Here is a sample config from the Cisco manual 3)
enable configure terminal interface GigabitEthernet1/0/1 monitor session 1 type erspan-source description "For TrisulNSM" erspan-id 101 ip address 10.0.0.21 mtu 1900 no shutdown
On MTU and packet sizes
- mtu 1900 – ERSPAN adds about 42 bytes of extra header bytes by way of Ethernet/IP/GRE header. The default ERSPAN MTU is 1500 bytes, so when you mirror full length packets they can be truncated. Make sure you increase the MTU of the ERSPAN to 1700 or 1900 or even the maximum size of 9000 bytes.
- You also need to set the MTU on any bridges you create on the VM infrastructure.
- If you dont set the MTU to a higher numbers, then packets will be truncated as per the ERSPAN documentation. Some implementations may fragment the IP packets, which will they place a load on the NSM tool to reassemble the packets.
to view the monitor
show monitor session 1
Enabling ERSPAN in TrisulNSM
Trisul Network Analytics supports ERSPAN natively since version 6.5.2883