Measure your network along a hundred axis
You cannot optimize or secure what you cant see ! Trisul generates hundreds of metrics at all layer of the network continuously, computes the most important views of these metrics, and stores them. All in real time. What you get is the world's best available visibility into current and historical network traffic. Your teams can COnfidently perform monitoring, reporting, incident response, and detection of metric outliers.
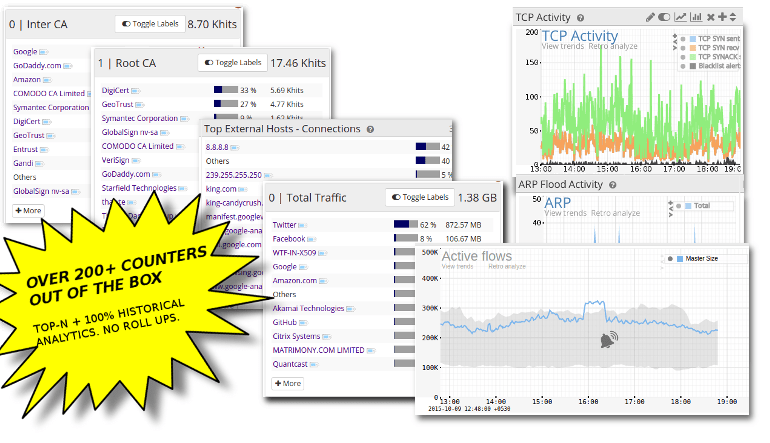
Benefits of maximum metrics coverage
Legacy network monitoring systems give you some basic metrics related to bandwidth usage on a port, IP, or protocol basis. These tools also tend to have a constrained backend database which leads to optimizations like summarization, rollups, discarding low usage items and such. When time comes to investigate you will find that the exact metric you need has been discarded as low value. Trisul takes a radical departure from this. Using advanced techniques Trisul enables even small businesses to generate and store millions of metric datapoints without any loss of resolution in a high throughput backend data solution. Trisul’s maximum metrics design gives you peace of mind and confidence.
360-degrees
Everything you care about is transformed into a metric. Reduce your blind spots.
Counters
Metrics are well organized into counter groups.
Algorithms
Stream algorithms Top-N,Bottom-M,First-Seen,Cardinality, Time Series, Flows
Customize
5 different ways to derive your own counter groups.
Layer 2
MAC, VLANs, Spanning Tree, MPLS
Correlate
Correlate counters with other counters,flows, or with Trisul EDGE graph analytics.
Smart alerting
Learn about bands of metric values, then alert on crossing.
Easy to customize
Five powerful tools to create your own business speciic metrics by point and click. Unlimited flexibility.
Filtered Counter Groups help you track a subset of a parent group by filtering by a second group.
Applications on Subnet 192.168.2.0/24
Takes the Applications counter group and filters it by the Hosts Counter Group with the filter criteria 192.168.2.0/24
Benefits
Zoom in on a particular set of items separately.
Keyset counter groups are a generic way to aggregate and count. This is known in some industry circles by the narrow rigid term “IP Groups”
Example : Count http,https,port 8080 as WEB
Take the Application Group then combine the keys http,https,8080 and assign a new key WEB to that group.
Benefits
Count aggregates rather than individual items for grouping purposes.
Only count items from a parent counter group where a metric value matches a control range.
Example : Intranet Applications
Takes the Applications counter group and filters it by the Internal Traffic > 0
Benefits
Only focus on items with certain metrics properties.
Flexible rules involving multiple counters
Example: Count all applications to Port 443 on IP 10.0.12.12 as SAP
Takes the Applications counter group and adds a Host based rule
Benefits
Adapt metrics to your organizations applications.
Cardinality meters can be added to any counter group. This allows you to count Unique X or Y.
Example: Unique applications for each Host
Takes the Hosts counter group and add Apps as the cardinality metric
Benefits
Monitor uniques
Use this to track metric flows. Formed by a cross product of upto 3 different counter groups.
Example: Internal-Hosts X Applications
Combines the Internal-Hosts and Applications counter groups to create a cross product;
Benefits
A powerful way to track information flows.
Why you need to measure everything
It might seem like deploying Trisul Network Analytics will let loose a deluge of analytics points that might be overwhelming. We have carefully designed the platform to keep the analytics coherently grouped with an intuitive internal structure. To get a grip on todays networks you need to deploy such multi layer visibility tools because of
- increasing crowd workloads – you need more sophisticated monitoring that can measure far more number of metrics than simple bandwidth numbers.
- pervasive encryption – more flow and traffic monitoring along with sophisticated TLS handshake monitoring provides the visibility.
- new threat profile – lesser and more dangerous. so you need to integrate threat intelligence into flow and metric data.
- flexibility needed – you need a platform that can integrate new analytics needs quickly. A recent CVE exposed vulnerability in processing of Elliptical Curve algorithms. This might mean you improve your visibility to start monitoring Elliptical Curve algorithms in general. Trisul supplies this crucial capabilities to your team.
- integrations – you need open API to integrate with other tools such as NIDS, Firewalls.
- fast long term analysis – the database must be capable of long term analysis over the entire spectrum of data points you have collected.
WIth Trisul Network Analytics you get all these capabilities in one integrated solution. You can conduct any type of visibility monitoring, detection, investigation, and audit needs confidently.