TRISUL NETWORK SECURITY MONITORING
Packet Based Monitoring for NBAD & NDR
Monitor, detect, and investigate all your networks in real time with Trisul NSM’s Network Detection and Response (NDR) & Network Behavior Anomaly Detection (NBAD) analytics.
Watch Our Video!
Explore Trisul Network Security Monitoring Solution's powerful features providing real-time traffic monitoring, raw packet analysis, hundreds of metrics and much more.
NETWORK SECURITY MONITORING WITH TRISUL
THREE KEY BENEFITS OF NETWORK SECURITY MONITORING
Visibility
Gain unparalleled insights with our advanced metrics on peers, TLS ciphers, and host-app links, enriched by metadata from files, DNS, HTTP, and certificates.
Detection
Investigation
Reconstruct and store flows for fast investigation, and uncover relationships between metrics using Trisul Edge graph analytics.
One Integrated Solution Lets You Focus On Visibility
Traffic Monitoring from a Security Perspective. This sets Trisul NSM apart from tools that only offer either traffic monitoring or security detection. By working on raw packets and extracting different data types in addition to deep traffic views gets you the full picture. The special feature is a sophisticated raw packet storage which gives you access to the actual packets.
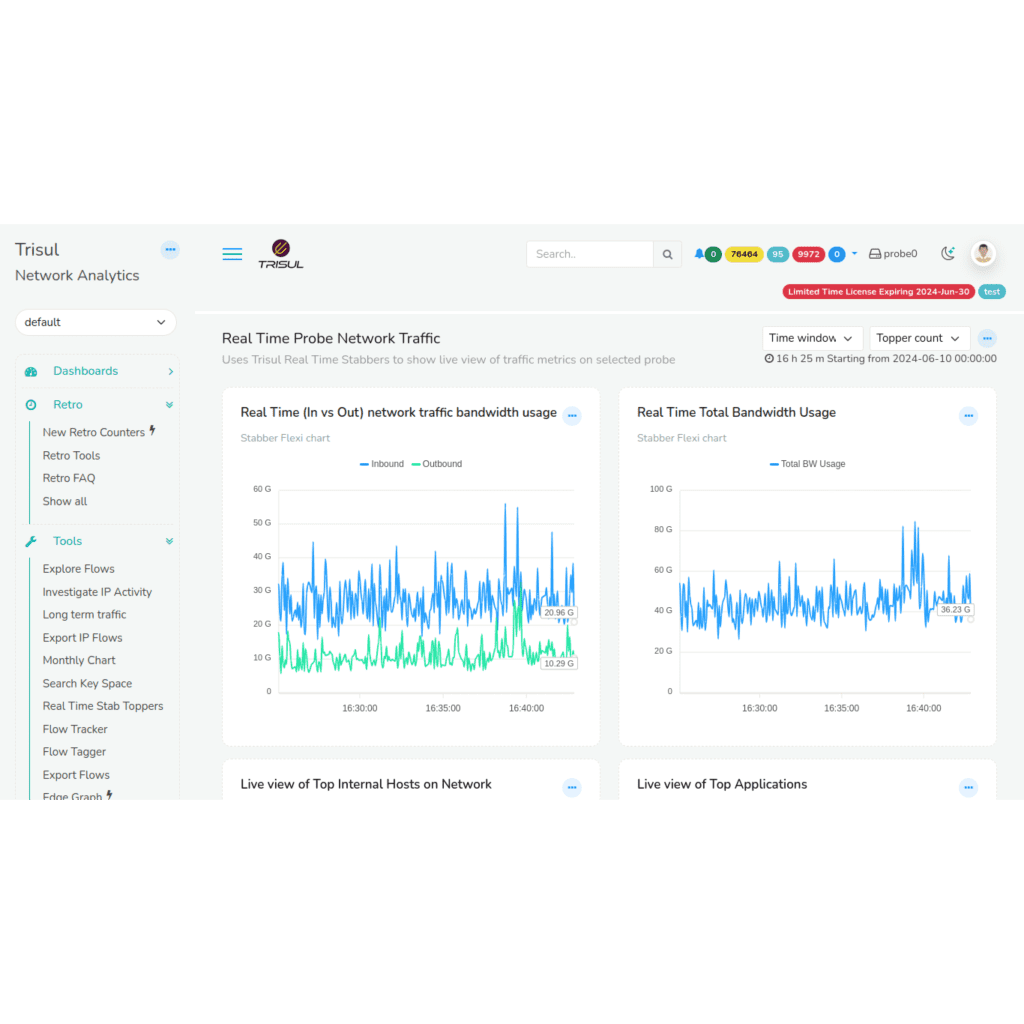
Deep and wide traffic metrics and top talkers
Raw packet analysis gives you wide visibility across layers
- Real Time Traffic Metrics
- 200+ metrics in 40+ counter groups out of the box
- Time series data stored for each item at 1 min resolution
- Advanced metrics like Unique-N, Top-N, Bottom-N, CrossKeys
- Point and click to create your own metrics
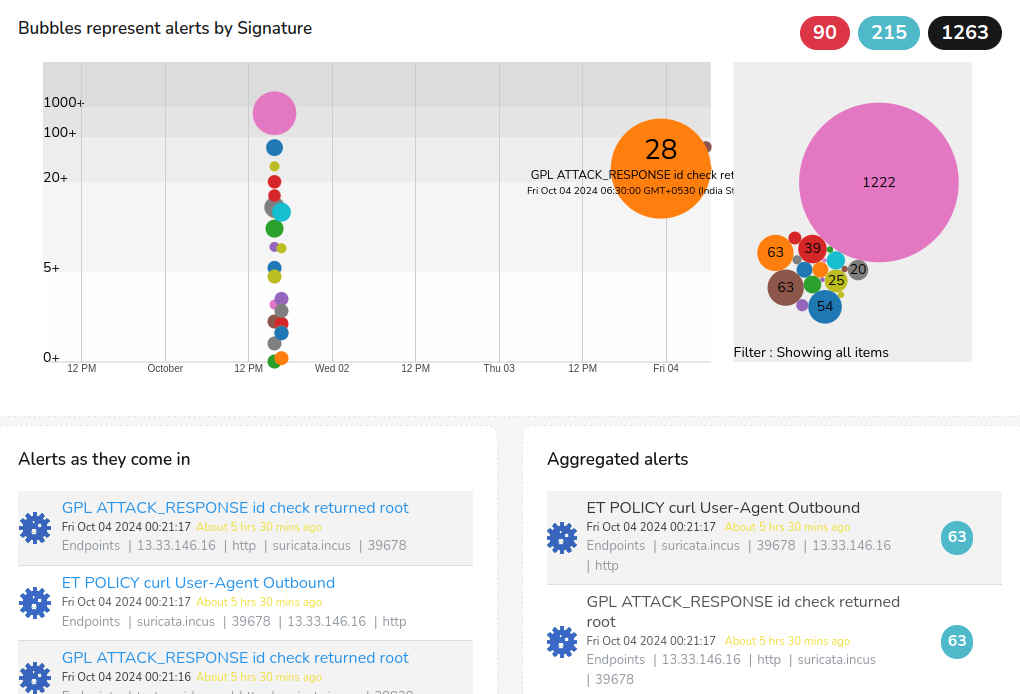
Real-Time IDS Alerts Dashboard
Integrated with signature-based intrusion detection
- Websockets powered real time alert dashboard
- Visualize large quantities of alerts with smooth, intuitive, dynamic animations
- Investigate further with drilldowns to visualize all event-related data in an interactive graph, showing related alerts and impacted IPs.
- Download complete packet capture (PCAP) files directly from the dashboard for in-depth analysis.
- View all flows associated with the alert, auto-tagged with IDS and country tags for efficient identification.
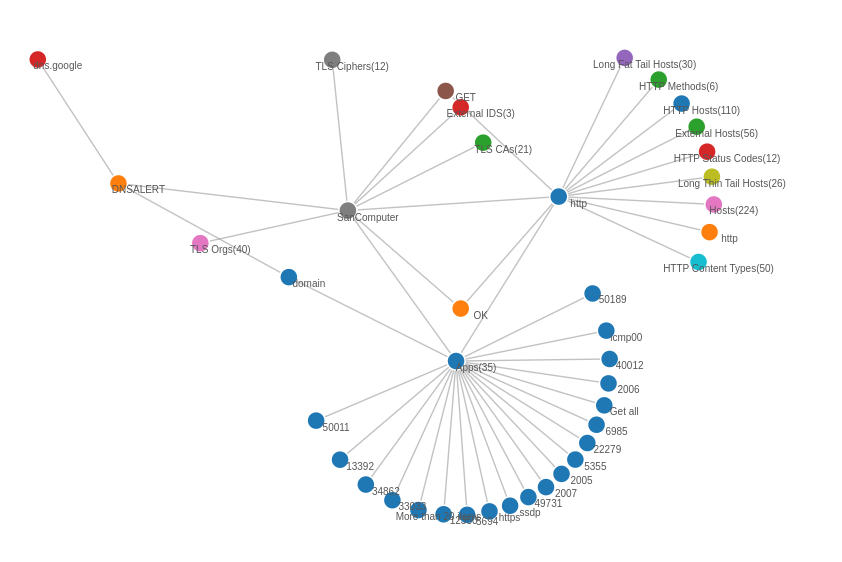
Edge Graph Streaming Analytics
Discover hidden relationships between various network metrics beyond traditional flow connections for deeper insights into network behavior!
- Explore how network entities like IP addresses, ports, protocols are interconnected.
- Go beyond basic flow connections by enriching flows with tags that reveal if TLS cipher suites, organizations, and countries are related.
- As Trisul captures packets, it generates an "Edge stream" in real-time, linking related entities for on-the-fly analysis.
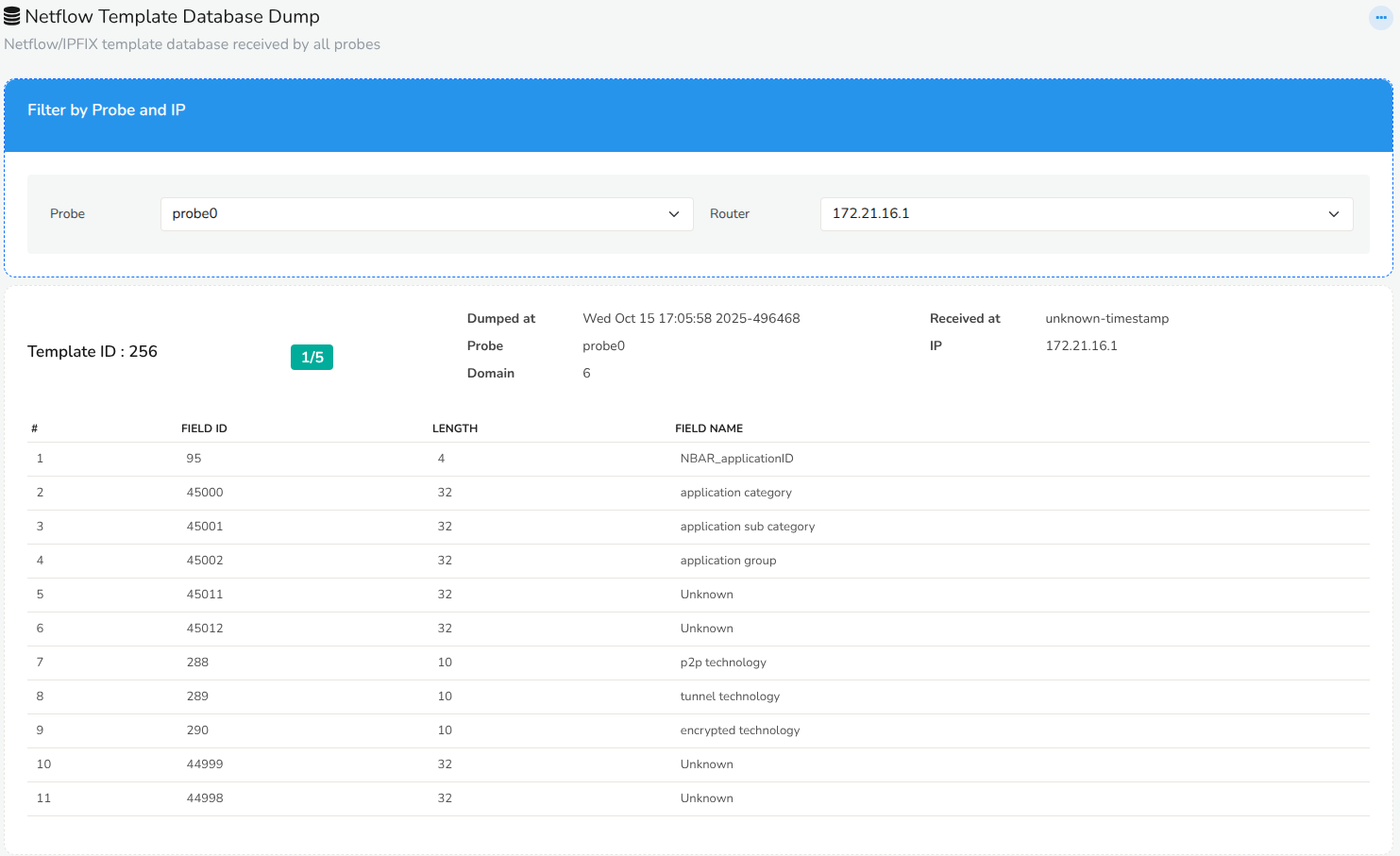
Automatic Packet to Flow Generation
Detailed flow visibility from raw traffic
- Generates rich NetFlow/IPFIX records directly from live packet streams, giving complete flow visibility even when network devices don’t export flows.
- Supports both full 1:1 flow capture and configurable sampling, allowing you to balance visibility, performance, and storage efficiency.
PRIORITIZE MY NETWORK'S SAFETY!
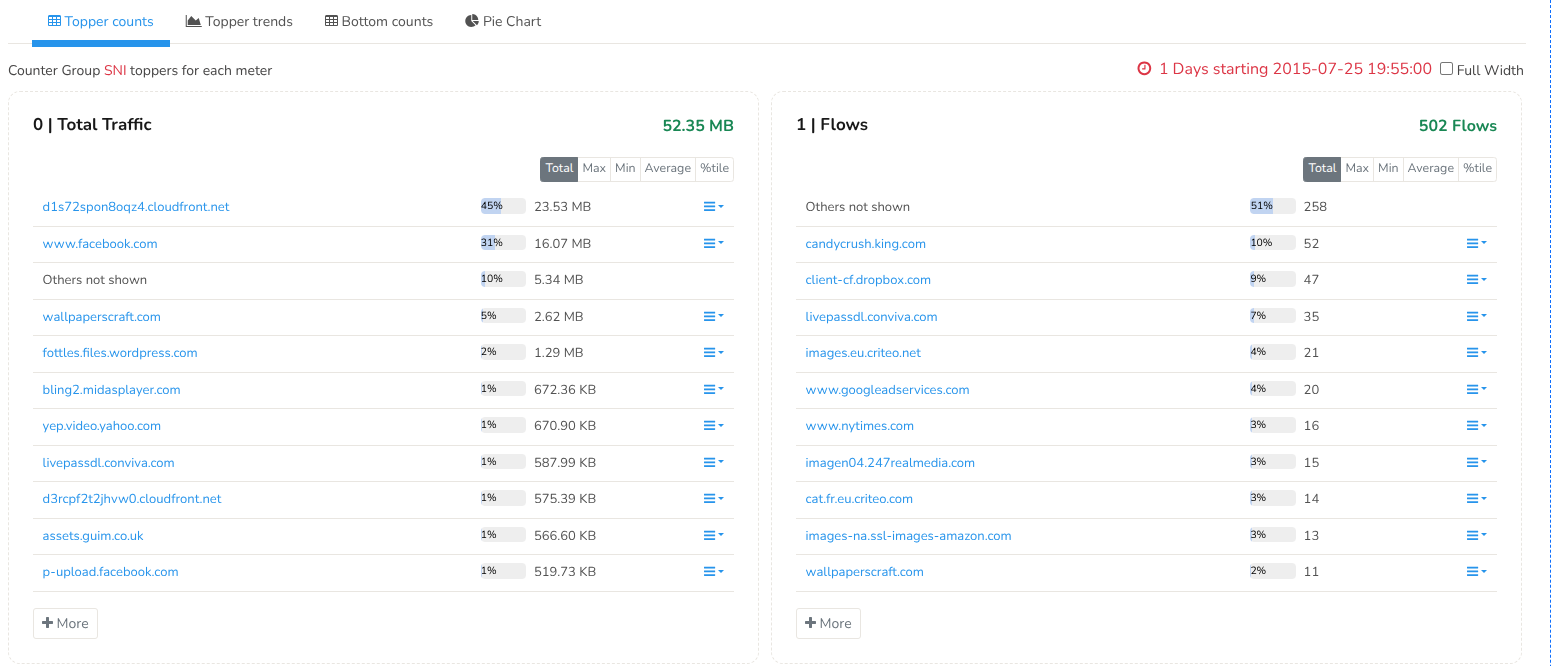
Analysis of Encrypted Traffic
Visibility into encrypted sessions without decryption.
- Extends visibility beyond standard TLS metrics by analyzing encrypted session behavior and identifying abnormal patterns.
- Using SNI data, gain deep traffic insights by cloud hostnames and applications, helping identify unusual encrypted sessions and tunnels such as GTP, GRE, IPsec, and MPLS, all without decryption.
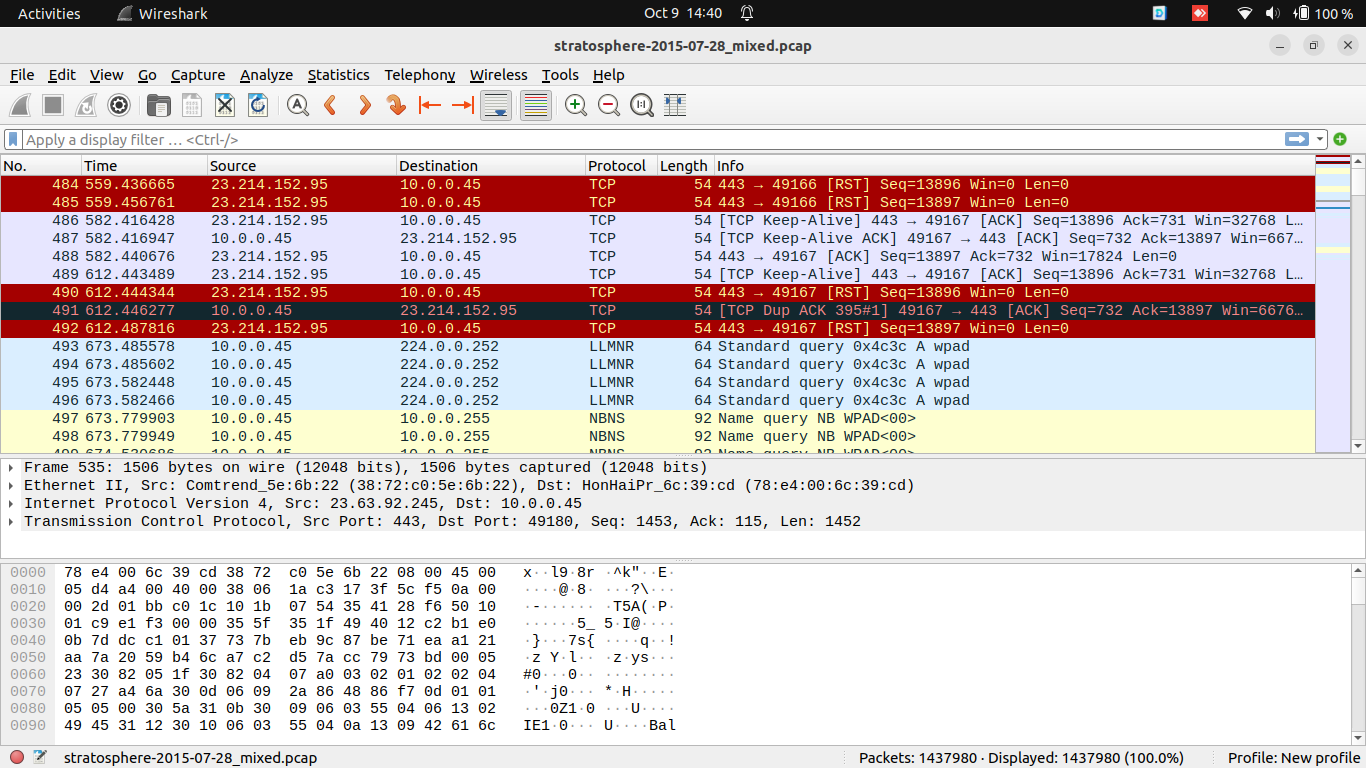
Raw Packet Analysis
Analyze raw packets with Trisul not only for improved network security monitoring but also for performance troubleshooting!
- Access full packet content in a single click for security applications, enabling you to analyze threats and anomalies effectively.
- Quickly retrieve ARP and Spanning Tree packets to diagnose Layer 2 issues and optimize network performance.
- Utilize the Trisul LUA API to customize packet storage policies at the flow level, tailoring your data retention strategy to fit specific needs.
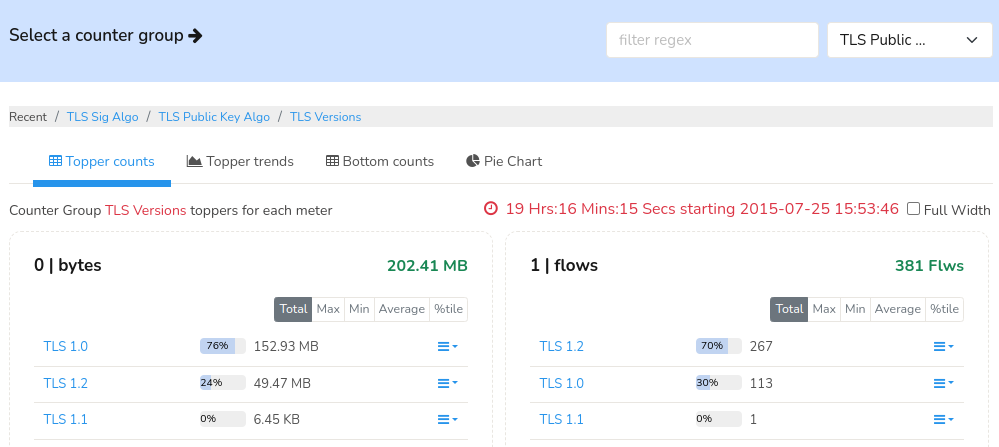
Advanced SSL/TLS metrics
Track and analyze SSL/TLS parameters for deeper encrypted traffic insights.
- Gain detailed SSL/TLS visibility by tracking protocol versions, cipher suites, certificate authorities, organizations, public key and signature algorithms.
- TLS certificates are hashed and checked against threat indicators to identify compromised or untrusted entities.
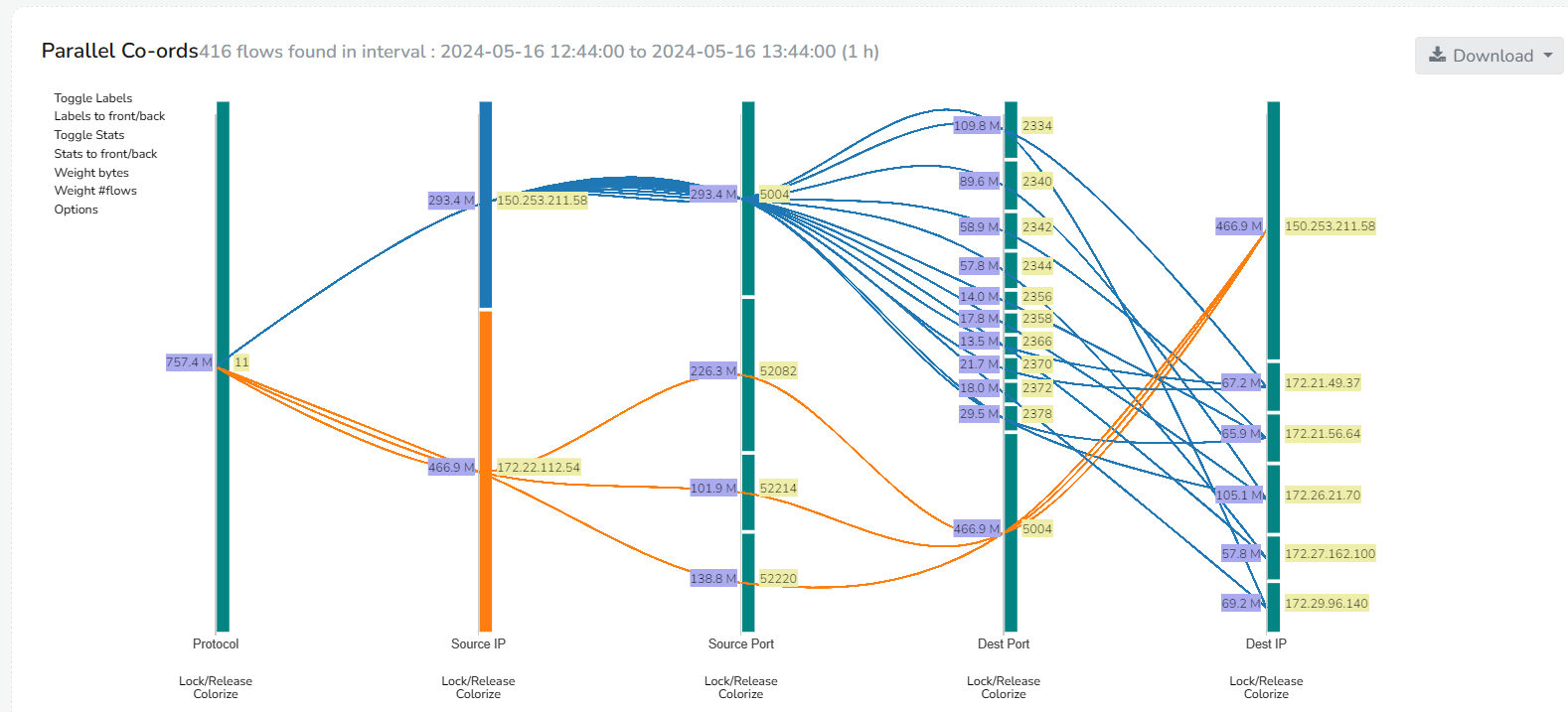
Track Each Flow
Store every flow to aid investigation
- Flow is a record of communication
- Construct flows from packets and store them
- Query flows for any IP for as long as you want
- Query flows for any IP for as long as you want, this provides a solid record which you can rely on when conducting investigations