TRISUL NETWORK ANALYTICS
NETFLOW AND PACKET MONITORING
NEW RELEASE 7.0.3199 ( September 2025 )
Feed us your NetFlow, Packets, BGP, SNMP, and Syslog. We’ll analyze, detect anomalies, and store for audits and swift incident response.
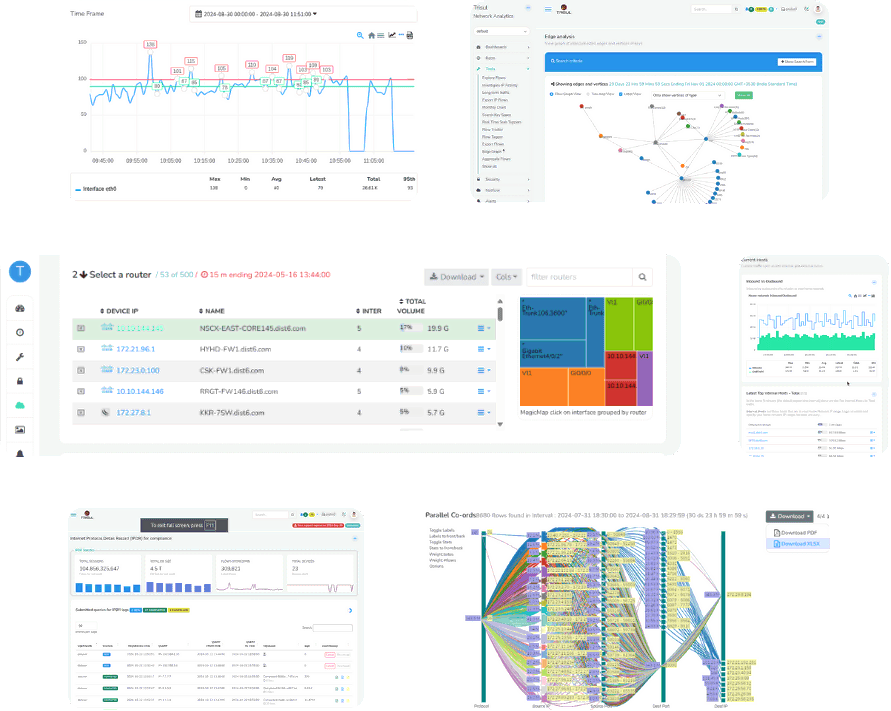
Four Solutions, One Powerful Platform!

Trisul NetFlow Analyzer
Effortlessly monitor network traffic with Trisul via NetFlow, SFLOW, or IPFIX and gain insights into network performance.

Trisul Network Security Monitoring
Collect, analyze, and investigate network traffic with Trisul. Plug-and-play security monitoring with built-in IDS.

Trisul IPDR DoT Compliance Solution
Trisul IPDR solution helps ISPs comply with regulatory mandates, storing IP flow logs at minimal cost.

Trisul ISP Peering Analytics
Gain real-time visibility into network traffic flows with Trisul’s peering analytics. Track volumes, optimize routes and more.
WHO USES TRISUL
- INTERNET SERVICE PROVIDERS
- SECURITY ANALYSTS
- LARGE ENTERPRISES
- NETWORK ADMINISTRATORS
HOW TRISUL CAN HELP YOUR ORGANIZATIONS
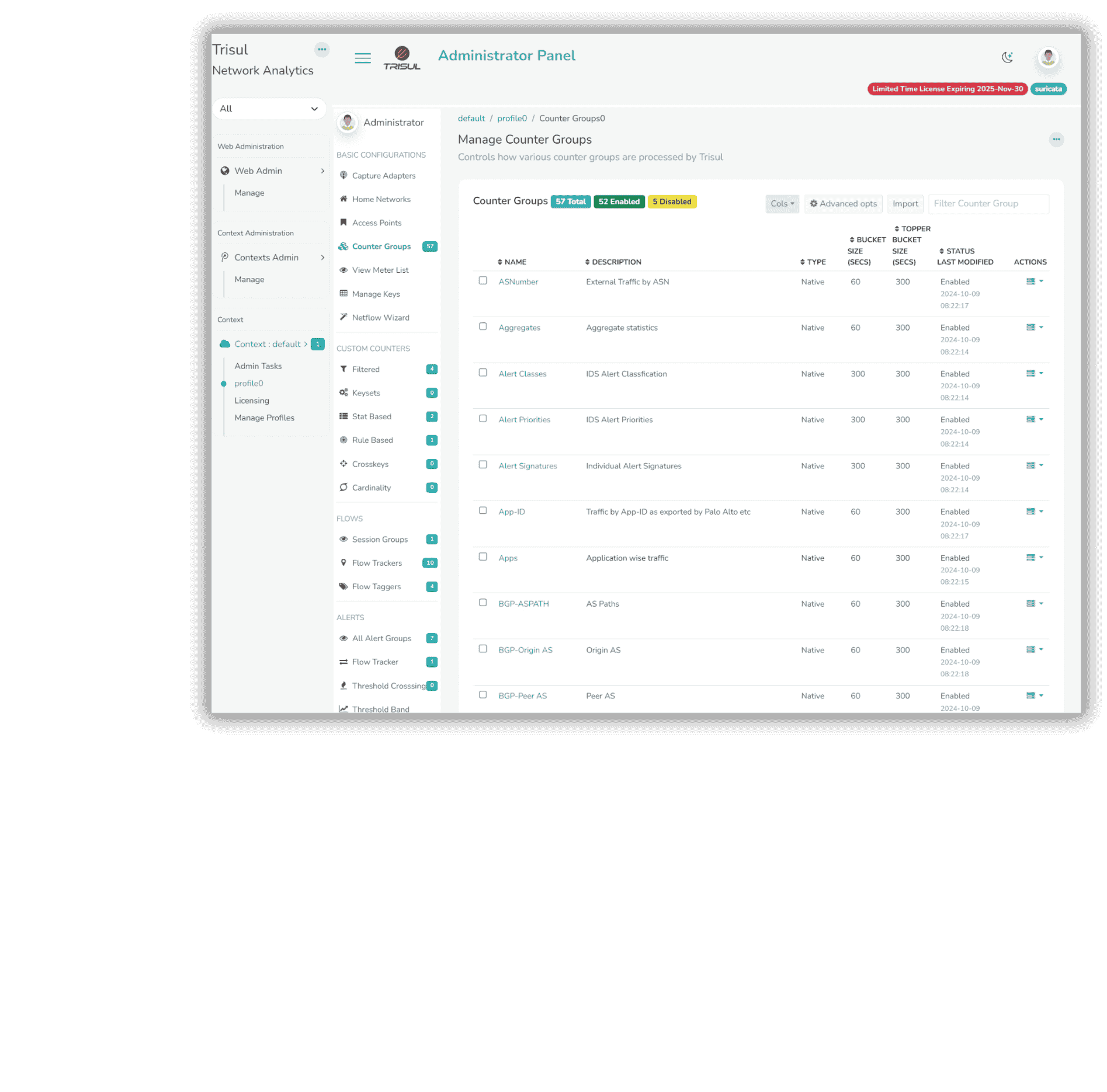
Metrics are the Baseline
Unlock 360-degree visibility into your system's performance with Deep Metrics Collection. This powerful feature gathers essential metrics, including App and host bandwidth, TLS certificate algorithms, Ethernet metrics, Geo-based insights, HTTP errors. Combined with advanced tooling like network flows analysis and graph analytics. This helps network teams to understand the behaviors in anomalous pattern and gain unparalleled investigation and detection capabilities in real-time.
- Hundreds of metrics for millions of entities
- Powerful built in algorithms. Top-K, Bottom-K,Cardinality, First-seen
- Powerful retrospective analysis tools for IR
- Ingest packets, netflows, snmp, or logs.
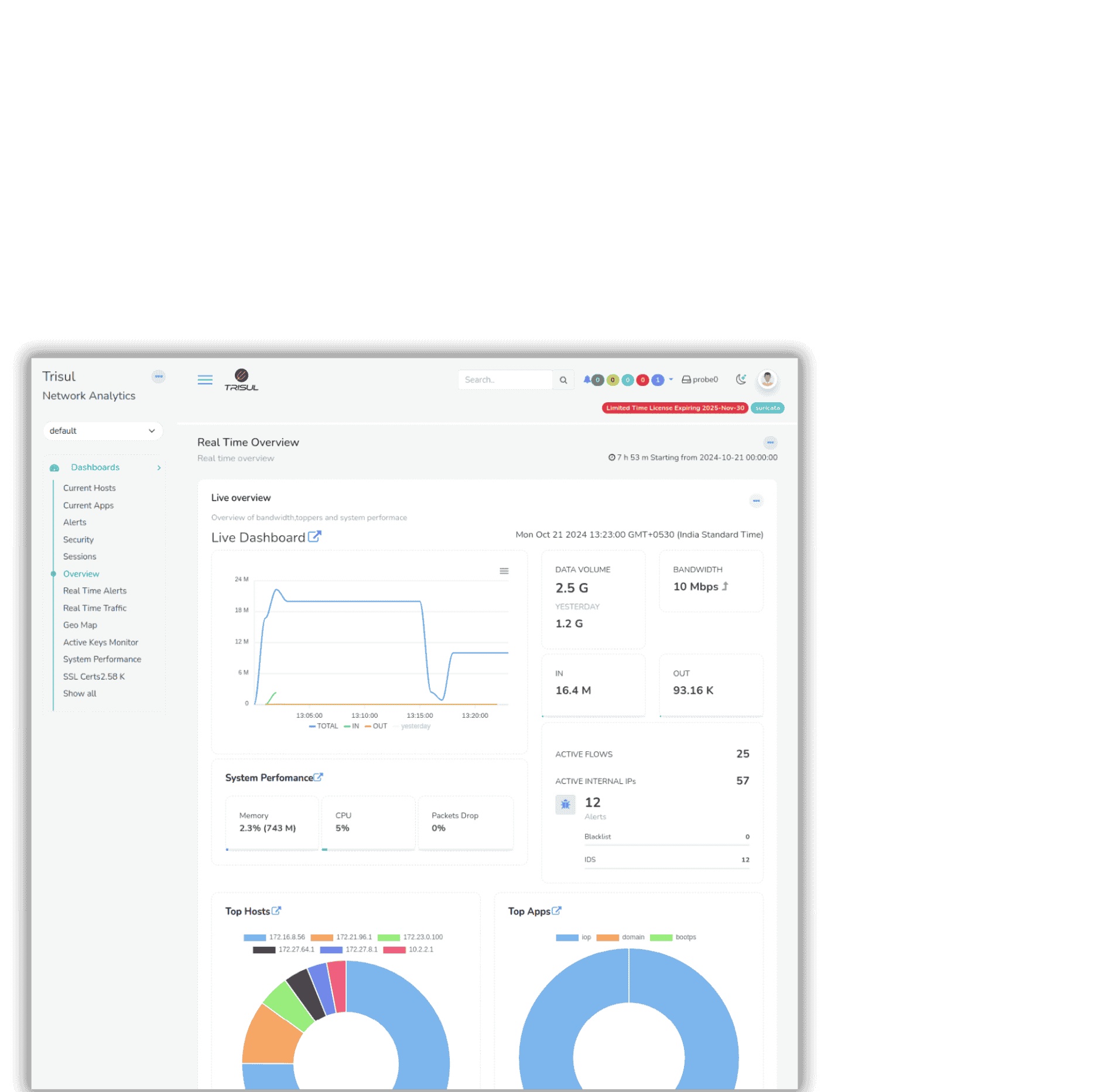
















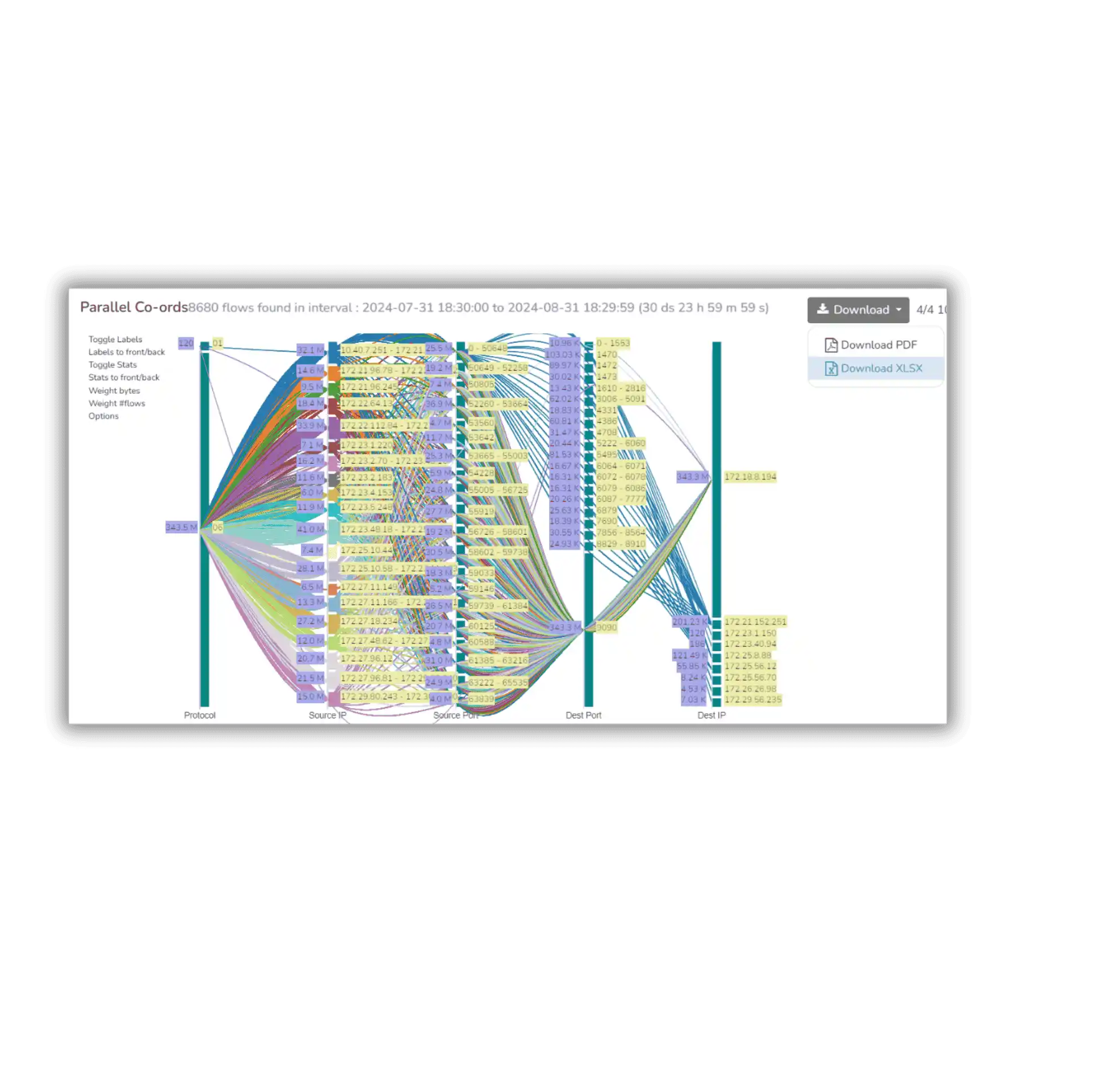

Never Miss a Flow
A flow is a unit of transaction between two network endpoints. Storing a record of every single flow is a foundation capability for investigations. Trisul Netflow makes it easy for organizations of every size to roll this out. You can mix and match - send packets at security perimeters and Netflow at internal core switches to track lateral traffic.
- Ingest Netflows or reconstruct flows from packets
- Flexible query language
- Flow Taggers : add searchable text labels to flow records
- Dont compromise ! no summarization or rollups
Are You Ready to Really Open Up your Network Traffic?
We include a free license that allows monitoring for a trial of 7-days. All you need to do is arrange a way to send traffic, netflow, or PCAP dumps to us. Our docker image makes it effortless to install on any linux platform. Just sign up and download, no credit cards or other commitments required.
