Improving visibility after the CVE-2020-0601 vulnerability
CVE-2020-0601 describes a vulnerability that exists in the way Windows CryptoAPI (Crypt32.dll)validates Elliptic Curve Cryptography (ECC) certificates. In short: your ECC certificates can specify known curves like prime256v1 or define your own with custom parameters. Sounds like trouble already! It turns out it is possible to pickle these parameters to clear the verification step.
When vulnerabilities like this come to light, the common reaction of security products is to scramble to release detection scripts. In Trisul’s metrics-first paradigm we try to identify new points of measurement and improve our visibilty.
Do we have this visibility ?
This vulnerability impacted ECC certificates with unnamed explicit parameters algorithm. But there are so many types of other public key algorithms , secp384r1? rsa? Curve22519? etc. If only we had these statistics already in place, we could have alerted on unusual ECC even without a CVE disclosure. We could even turn into those who spot and report the vulnerability. Now, that would be cool 🙂
The question we ask
Can you tell what kind of certificates are seen in the last 24 hours ?
Most security teams are likely to come up empty. In Trisul’s metrics worldview, it is not enough to deal with the vulnerability but fix this newly revealed visibility blindspot.
- Forward : Setup new monitors to fix the visibility blindspots
- Retrospective : Scan past activity to check for this vulnerability and to hunt in nearby areas. Say look for outlier named curves while searching for explicit parameters. Maybe you’ll find something there.
Today, we are releasing scripts to help with these two approaches.
New Trisul APP: TLS Metrics Pack
We are releasing a new app today called TLS Metrics Pack which closes the blindspots mentioned above. See the GitHub page TLS Metrics Pack for details and instructions. Go for the visibility win.

Closing the blindspots with the TLS Metrics Pack APP
Until now Trisul metered the following TLS Metrics – SNI, TLS Cipher Suite, TLS Organization, TLS Root and Intermediate CA. In response to this vulnerability we add TLS Public Key Algorithm, while we are at it we also add TLS Signature Algorithm. Another important metric that was missing was TLS Version.

Edge analytics
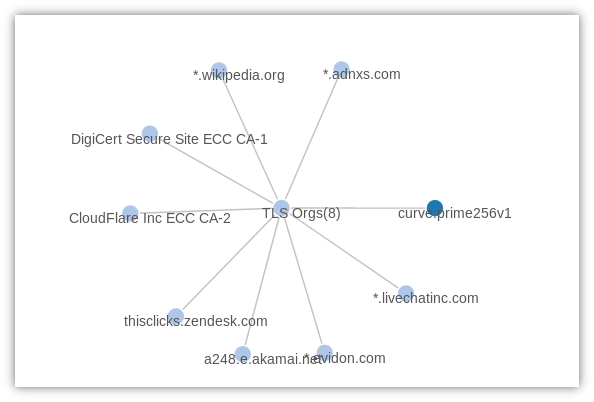
One the killer features of Trisul is EDGE graph analytics. It helps you discover relationships between metrics. It is optimized for sparse graphs which is where most of the analyst interest will lie. The following image shows how we discovered which organizations are using the prime256v1 ECC cert.

Retro analytics
The Trisul Remote Protocol API empowers an analyst to automate analysis tasks on historical data. The H word – hunting expeditions 🙂 Today we release a Ruby Script that incrementally searches your entire TLS Certificate Database to check if any explicit EC Curve certificates were found and statistics of cert algos in use. The script is freely available at https://github.com/trisulnsm/trisul-scripts/tree/master/trp/cert-search
Look what we found , one of our team members was checking out the SANS test website
Copy secp384r1/unnamed_explicit_curve SANS ISC DShield Test/INFIGO
We hope you find the new APP and the script useful, now I particularly like to keep watch of TLS 1.3 adoption rate.
Trisul API developers can use the released code to extend and innovate even further.
Check out our LuaJIT API for the coding parts.


Download Trisul today. Don’t just monitor, start NSM-ming !