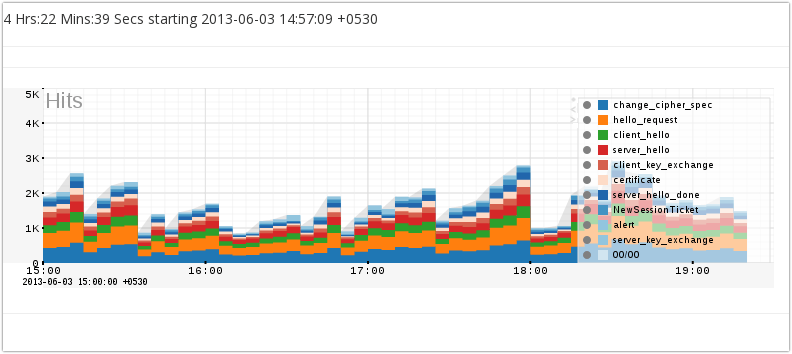
Monitor TLS Record types as a response to Heartbleed
What would be an appropriate detection strategy in the wake of the TLS Heartbeat based attack ? The most popular response is to incorporate the newly released Snort /Suricata IDS signatures into your ruleset. While this is a good thing, do these new signatures add to your overall visibility into the nature of TLS traffic in your network ?
Trisul enables long term statistical metering of the nature of traffic.

tls-monitor.lua
We have released a tiny LUA script on Github called tls-monitor.lua that adds monitoring of TLS Records.
- Add a new counter group called “TLS Record Types”
- Meter all content-types IANA Registry
- Meter all unencrypted handshake-types. We use a type/length heuristic to determine if the TLS handshake is encrypted.

Announcement about LuaJIT
We have moved to LuaJIT from Lua 5.2 in our latest builds. All the sample scripts should work fine. We have added utility classes for bit manipulation to T.util because the bit32 library of Lua 5.2 is not available in LuaJIT.
Other TLS based counters
Trisul’s other TLS based out of the box counter groups are
- TLS Cert Authorities both root and intermediate (Verisign, Comodo, ..)
- TLS Orgs (google, twitter, ..)
- TLS Cipher Suites
Stay safe !

Free Download Trisul 4.0 !