Searching for APT1 indicators with Trisul
The APT1 Report released by Mandiant last month has put up a lot of indicators in the public domain. This is exciting stuff for a lot of “intel starved” enthusiasts like us. Atleast three types of indicators can be searched for by looking at past network traffic.
- MD5 Hashes of malware or other supporting content
- DNS names
- SSL Certificates
Those running Trisul can easily validate if they’ve been hit. Here’s how you do it.
MD5 content matching
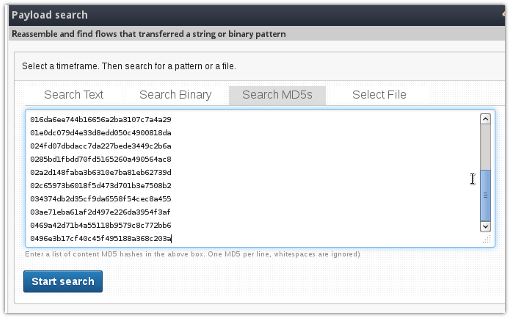
- Open Tools > Payload Search
- Switch to the Search MD5s tab
- Copy paste the entire list of MD5s into the box
- Press search
! Dont feel shy. You can enter thousands of MD5s in the box – the performance does not depend on how many you are matching

The result page contains all the flows which have matching content. Click on “Packets” to pull out all these flows into a tool like Unsniff or Wireshark to save the actual contents.
Inline vs Offline
Trisul matches all content types transferred over HTTP, not just EXEs or JavaScript. This is done by going back to the encrypted packets and looking at HTTP flows after dechunking and decompression. This may seem like a slow process that requires a lot of memory, but Trisul does this efficiently. On a lowly Intel ATOM Dual Core appliance we were able to achieve 250MB/s. One school of thought would do the HTTP normalization in-line and reduce the problem to a blazing fast log analysis. We think there is greater flexibility in offline analysis.
What if you had SHA-1 hashes in the indicators ? Offline post-hoc analysis can accomodate any type of and any number of analysis without requiring major upfront investment in CPU power.
Scripting this stuff
You can also do this programatically by writing a tiny little Ruby script. The script is available on the trisul-samples Github site. What is really cool about the searchMD5_adv.rb sample is – PCAPs are automatically pulled out when matching MD5s are detected.
Domains
- Open Security > DNS Resources
- Open the Search form
- Copy paste the entire set of FQDNs into the Resources list box
- Press search

Certificates
At present there is no way to do this from the web interface. You can however try the cert_extract.rb script This pulls out all certificates into Unsniff, you can then check for matches inside of that script.
Heads up
We are working hard on Trisul 3.0. Even cooler features and a brand new UI !! We welcome early beta testers who are willing to stress the product out.

Download Trisul 2.6 for Ubuntu or CentOS today.