Using X-Drill in Trisul 3.0 to hunt down DSA certificates
A quick introduction to the X-Drill (Cross Drill) tool in Trisul 3.0 .
We want to
– Track SSL traffic by certificate type (RSA,DSA,ECDSA)
– Track down services using ECDSA certificates
Full processing upfront vs half upfront / half retro
The logging approach taken by tools like Bro would simply make available the certificate type in the log. The above question is simply a matter of scanning the logs for ECDSA attributes. Because the processing is up front, all attributes of interest have to be known ahead of time.
Trisul takes a different approach – half upfront and half retrospective analysis. The TLS Cipher counter group tracks the different ciphersuites over time. If you want to explore a specific cipher suite further – you will use a tool called X-Drill. This tool replays the raw packets by taking advantage of the timeseries knowledge of the cipher suite of interest.
The advantage of X-Drill is you dont have to know all the permutations before hand, so arbitrary analysis is possible. Finding out all Countries using ECDSA is the same complexity as all Hosts using ECDSA.
X-Drill step by step
Traffic by Cipher Suite
Select Retro → Retro Counters , then select a timeframe and select TLS Ciphers from the dropdown to bring up the following.

The table on the left is the traffic volume per TLS CipherSuite. On the right, we have the number of flows. For example – the image shows that in 4 Hrs 45 Minutes we had 15.53MB of SSL traffic using RSA_WITH_RC4_128_SHA and 448 flows using the same.
From the above picture we see almost all SSL flows use the RSA certificates. But we also see some activity (hi-lited) for ECDSA. Now we’re intrigued and want to find out who is using this rare certificate type.
X-Drill into hosts
Press the X-Drill button next to the row that says ECDSA, it will bring up a dialog that prompts you to select what to X-Drill into.

Go ahead and select the Hosts counter group to see which hosts are using this particular type of certificate.
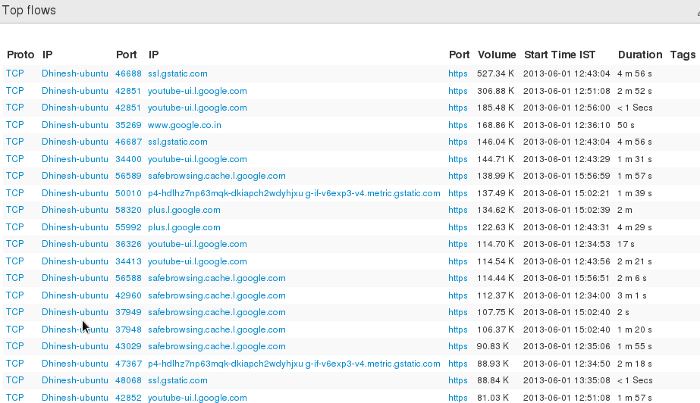
Results
The X-Drill tool will now churn through the packets looking for Hosts controlling for the ECDSA certificate type. You get the following output.
- Time series traffic chart
- Top Hosts
- 200 Top Flows



You have now solved the mystery. The user of ECDSA certificates in our network is Google. They seem to serve static assets from youtube, gstatic, safebrowsing etc using ECDSA while retaining RSA for normal GMail and other dynamic services.
Trisul X-Drill turns what would be an incredibly difficult analysis into a Meh! task.

Download Trisul today.