This is an old revision of the document!
Table of Contents
Processing the DEFCON 26 CTF PCAPS using Trisul NSM
With the right tools, analyzing large PCAP dumps can be lots of fun. This article is a step-by-step of using TrisulNSM to dive into the DEFCON26 CTF PCAP 1)
Given only a large PCAP dump, your first task as an analyst is to make sense of it from multiple angles. I typically like to start off with a statistical overview.
- What is the timeframe of the CTF?
- What was the bandwidth used over the time duration ?
- What were the top IPs as attackers and as targets?
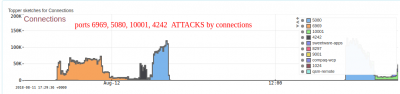
- What ports were targeted?
- Any red flags from IDS like Snort/Suricata over the duration?
- Top flows download/upload
- then once you have a baseline, You can follow several tracks to investigate in depth. Down to the packet level.
TrisulNSM (Trisul Network Analytics) is the leading platform today for performing this kind of analysis over very large PCAP files. This article describes how you can use our free docker image trisulnsm/trisul6 to slurp this PCAP and then have some fun analyzing it. The docker image runs a 2-pass analysis with TrisulNSM and then with Suricata and then presents a unified analysis.
Get started
So,lets get started. We assume you have a fairly decent Linux machine ready with Docker installed. Any distro will do because we are going to be using our Docker image.
- Download the DEFCON26 PCAP , a 5GB file into a directory.
- Unrar the file and extract the inside PCAP into a filename without spaces such as
dc26ctf.pcap - Create a directory on your system where the results will be stored. Move the PCAP to that directory so the docker container can see the PCAP file.
mkdir /opt/trisulroot mv dc26ctf.pcap /opt/trisulroot
Run the trisulnsm/trisul6 docker image over the PCAP and run the webserver over port 4000.
sudo docker run --privileged=true \ --name=trisul1a \ --net=host -v /opt/trisulroot:/trisulroot \ -d trisulnsm/trisul6 \ --pcap dc26ctf.pcap \ --webserver-port 4000
You can check the docker logs if the process kicked off successfully.
docker logs trisul1a -f
If there are no errors here, it means the process has been kicked off. Expect anywhere from 20 minutes to an hour depending on your computer's CPU/Memory/SSD configuration 2).
To monitor the progress login to the container and do the following.
root@unpl:~# docker exec -it trisul1a /bin/bash docker$ # to view process usage docker$ top docker$ # add helper macros for trisul docker$ source /usr/local/share/trisul-probe/trisbashrc dc26ctf1 docker$ # tail the log files docker$ tailf.ns
You might want to take a break and have a coffee !! When you get back you can login to http://ip:4000 to analyze the fun stuff.
Screenshots
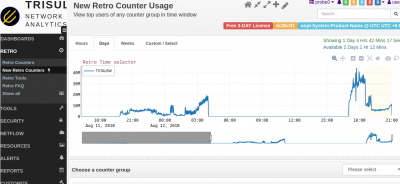
Timeline showing volume of traffic between 10 and 100Mbps over the period of the competition. You can select any timewindow and drill down
Trend
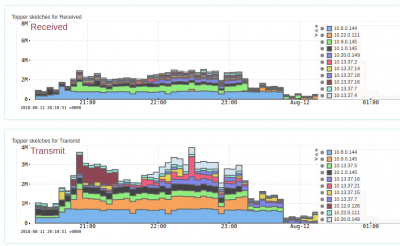
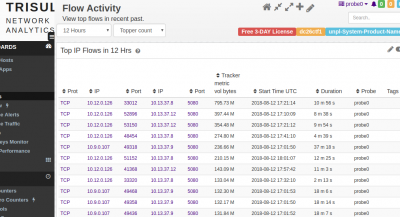
Top flows
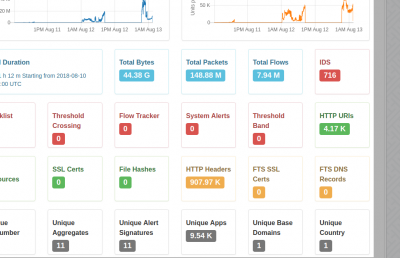
PCAP totals dashboard
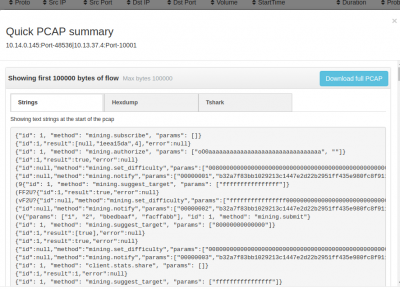
Exploring HTTP Status 123
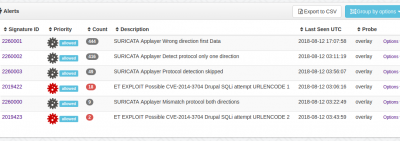
Alerts, attacks on Drupal
Pivot to packets from anywhere
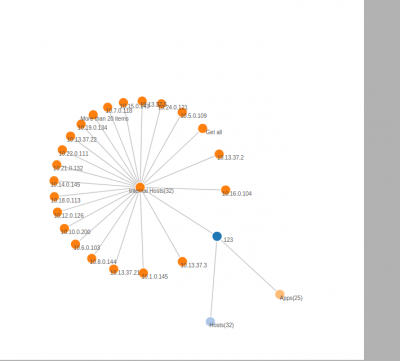
Conversations of a particular hosts
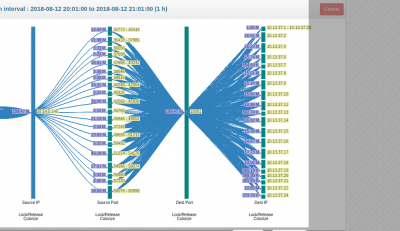
Port connections over time