This is an old revision of the document!
Detecting covert channels in X.509 Digital Certificates using the Trisul LUA API
I saw a couple of blogs about a new way to create a C2 (Command and Control) channel using X.509 Certificates. This technique is described in Abusing X.509 Certificates for Covert Data Exchange 1) and the original link on the Fidelis Blog Whats missing is in front of us 2) and also on the Network Miner blog Examining a X.509 Covert Channel 3) I'd also like to mention the author Jason Reaves
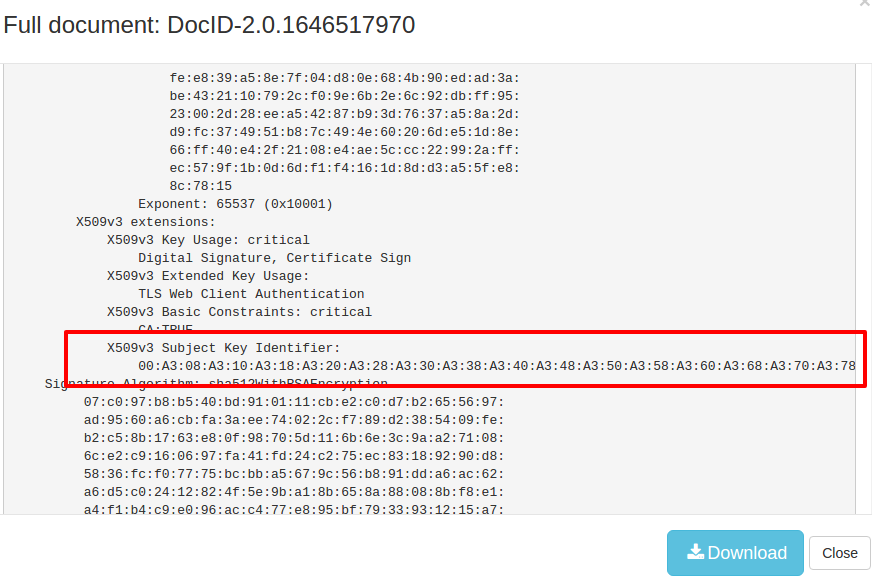
In this technique the covert channel is built by stuffing chunks of data into X.509 Certificate Extensions, in this case the “Subject Key Identifier” aka SKI extension. This is usually a hash of 20 bytes. However this is not used in certificate validation and it appears from the researchers that the network defenses are not checking if this contains a valid value. The C2 POC uses a large number of certificates with SKI values of 10,000 bytes !
Detecting this is quite easy with Trisul as well as Bro IDS. This post highlights the different approaches taken.
The Full Text Search FTS Document
Trisul extracts metadata from network traffic and makes them available to LUA Scripts. There are two streams your scripts can plug into.
- the Resource stream: these are shorter summaries of the meta data. For example the DNS Resources would be one line summary of question and answers
- the FTS stream: a complete text dump of the meta data. The DNS FTS stream would be a full dump of all DNS fields - much like the DIG format. Similarly for SSL Certificates, the FTS stream passes text documents that mirror the `openssl x509` command.
You can see the different approach taken by Trisul NSM compared to Bro IDS. Instead of fine grained events, Trisul provides a text document.
PCAP