Table of Contents
Using Palo Alto User-ID and App-ID in Netflow analytics
Palo Alto firewalls are capable of exporting two very useful pieces for information in its Netflow export. The User-ID1) and App-ID 2) fields are added per-flow
- User-ID : harvested from a number of mechanisms to map IP-Addresses to user names. The primary method is to interface with Microsoft Exchange / AD servers.
- App-ID : the firewall deploys some heuristics to identify exact traffic types (eg Facebook, Google, Whatsapp)
These two fields really turbo charge your visibility and investigation capabilities. This article explains how to leverage these in Trisul Network Analytics.
- monitoring overall traffic of Users and Apps
- searching individual flows for a particular User or App at flow level
- aggregate statistics of a particular User or App.
Monitor overall traffic
New Counter Groups : User-ID and App-ID
Trisul automatically creates two counter groups called User-ID and App-ID. These meter the following metrics at the global level.
| meter | description |
|---|---|
| Total traffic | Total traffic bandwidth used by a User or App |
| Download traffic | Download bandwidth used by per User/App. The Download direction is metered when the flow source IP is an external IP address and the destination-IP is internal. Internal IPs belong to the Home Network configured in Trisul |
| Upload traffic | per-User bandwidth out of home network to external |
| Internal traffic | per-User bandwidth where both the source and destination are inside the home network |
| Transit traffic | where both source and destination are outside the home network. You will typically not find data here in normal enterprise environments |
| Flows | Total number of flows active per user/app |
To view these metrics
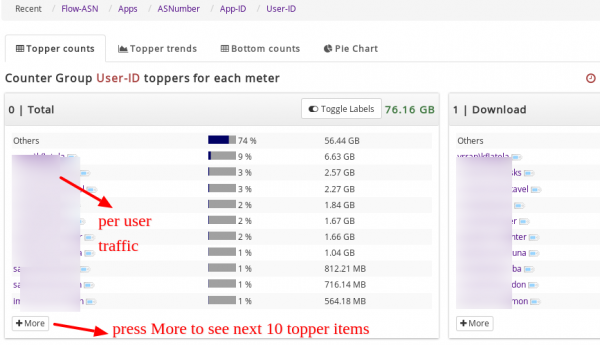
- Use Retro Analysis : Select Retro > Retro Counters then select a time frame, then select User-ID from the list of counters shown on the right side. You can see the top items for each metric.
- Create dashboards : Customize > UI >Dashboards > Create a new dashboard. Give it a name. Then Press the + button to add a new module. Clone “Current Top Hosts” of type “current toppers in a list”. Then edit to module to change to User-ID and Metric 0.
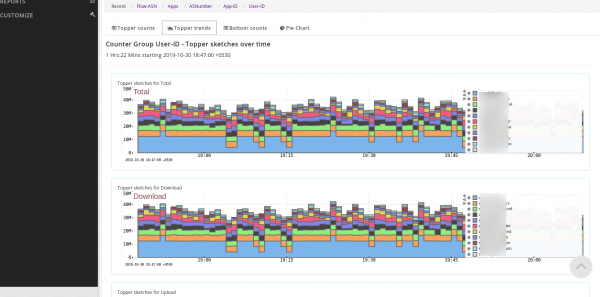
The retro analysis screen looks like below.
The Retro Analysis tools show you the Top-N, Bottom-N, Topper Trend over time, and Pie chart views. The following chart shows you toppers over time.
NAT issues
The default behaviour is to show the Internal and External IP addresses. The NAT is hidden from Trisul , if you wish to see the NAT'd firewall address set the following parameter to FALSE in the Netflow configuration file
<UsePostNATAddresses>False</UsePostNATAddresses>
Query by user-id and app-id
The next step is to create a flow tagger that adds the User-ID and App-ID to every flow stored in Trisul.
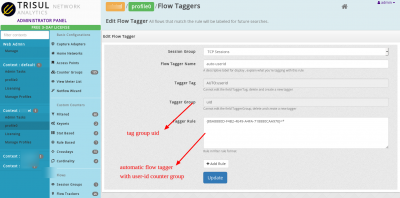
Login as admin, then go to profile0 > Flow Taggers > Create a new Flow Tagger. Then create an AUTO:userid flow tagger (see docs) to add the User-ID counter group keys to the flow. Use a Tagger Group of user as shown below
Do the same for App-ID. Now restart Trisul. From this point every flow will be tagged by the User-ID and App-ID.
Query flows
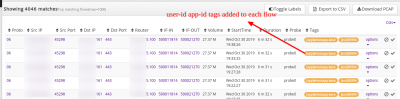
From Tools > Explore Flows
Use the syntax tag=[user]red\mike to query for flows from user red\mike
or tag=[app]whatsapp-base to query whatsapp flows.
Aggregate flows
From Tools > Aggregate Flows
Use tag=[user]red\mike to aggregate for flows from user red\mike
This shows top IPs, top Applications, and other aggregated information for the user. A complete picture.
A sample is shown below.
Conclusion
User-ID and App-ID attributes open up very powerful possibilities for visibility and investigation. Using the flexible tools offered by the Trisul platform you can customize in a variety of ways. Other tools you can use are “Filtered Counter Groups” if you want to zoom in on a particular user or app, “Cross keys” to monitor User App dataflows, “Flow Trackers” to zoom in on top flows from a particular user, etc. The scripting API also offers unlimited ways to craft your own tooling.