tips:suricata-eve-unixsocket
This is an old revision of the document!
Table of Contents
Suricata-EVE-Unixsocket
This article provides instructions for installing Suricata-Eve-Unixsocket app in Trisul Network Analytics. The Suricata-Eve app allows you to integrate Suricata IDS alerts into Trisul metrics framework.
Installation
1. Installing Suricata App
- You can install the app by logging in as admin and selecting Web Admin > Manage > Apps > Suricata via Eve Unixsocket.
2. Installing Suricata
Please install Suricata by running the following command,
add-apt-repository ppa:oisf/suricata-stable sudo apt-get update apt-get install suricata
3. Installing Emerging Threat Rules 5.0
- You have to install the Emerging Threats Community which are a set of rules that trisul will listen to.
- Download and install Emerging Threats Open rules into /etc/suricata
#cd /etc/suricata #wget https://rules.emergingthreats.net/open/suricata-5.0.0/emerging.rules.tar.gz #tar xf emerging.rules.tar.gz
Please ensure that you run these commands in root
4. Enabling EVE_unix Socket
- locate the 'Outputs' section in /etc/suricata/suricata.yaml enable EVE logging as shown below.
# Extensible Event Format (nicknamed EVE) event log in JSON format
- eve-log:
enabled: yes
filetype: unix_dgram #regular|
filename: suricata_eve.socket
The Filename is 'suricata_eve.socket' is the name of the Unix Datagram socket file that Trisul will listen to later.
- And, also disable the 'fast.log' in /etc/suricata/suricata.yaml as shown below.
outputs:
# a line based alerts log similar to Snort's fast.log
- fast:
enabled: no
filename: fast.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram'
5. Starting Suricata
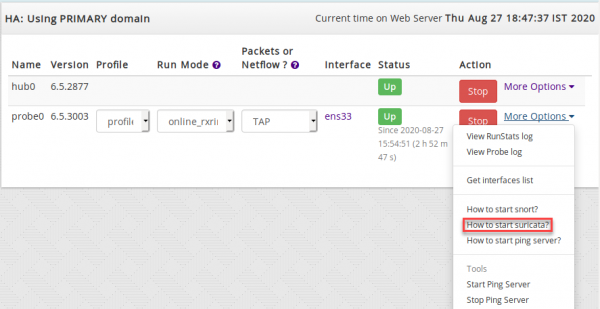
- Login as Admin and Select Admin Tasks.
- Click on 'More options' dropbox at the end of probe0.
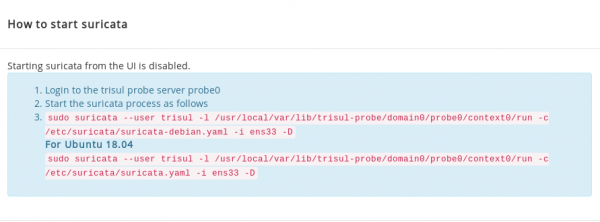
- You will find a Dialog box with command line to install Suricata as below.
sudo suricata --user trisul -l /usr/local/var/lib/trisul-probe/domain0/probe0/context0/run -c /etc/suricata/suricata.yaml -i ens33 -D
Please ensure you enter the correct Interface name.
6. Updating with latest rules
If you have already installed suricata and you want to update with the latest rules. Use the following command.
sudo suricata-update
tips/suricata-eve-unixsocket.1598535296.txt.gz · Last modified: 2020/08/27 19:04 by navaneeth